
Here we will discuss some of the types of cryptography used by different countries during World War II.
United Kingdom
TypeX The TypeX machine was a British cipher machine used from 1937 until the 1950s when it was replaced by more advanced methods of improvements. It was based on the commercial Enigma machine but with improvements that made it more secure, such as having five rotors. The first two rotors were stationary and would not be changed daily, which made it more secure without increasing the complexity of the machine. The main improvement the TypeX had over the Enigma was that the rotors had notches that would turn the adjacent rotor. This removed a weakness that was present in the Enigma as its fixed notches caused patterns to appear that would be noticeable under certain conditions.
Poem Code
The poem code was a cryptographic method used by the Special Operations Executive to communicate across Europe. This was done by having an agreed upon poem known to both the sender and receiver. The sender would pick words from the poem as the key and the words had letters that indicated that they are a keyword (the first word corresponds to A, the second is B and so on).
Example:
The poem is;
I compare thee to a summer’s day?
Thou art more lovely and more temperate
The keywords are:
I, to, day, art, temperate
The indicator group:
BEHJO
The keywords would be written out and numbered alphabetically to form a transposition key. The plaintext would then be written in the columns and the plaintext would be rewritten with the letters in each column in order with the indicator group written at the beginning.
Example continued:
The TypeX machine was a British cipher machine used from 1937 until the 1950s when it was replaced by more advanced methods of improvements. It was based on the commercial Enigma machine but with improvements that made it more secure, such as having five rotors. The first two rotors were stationary and would not be changed daily, which made it more secure without increasing the complexity of the machine. The main improvement the TypeX had over the Enigma was that the rotors had notches that would turn the adjacent rotor. This removed a weakness that was present in the Enigma as its fixed notches caused patterns to appear that would be noticeable under certain conditions.
Poem Code
The poem code was a cryptographic method used by the Special Operations Executive to communicate across Europe. This was done by having an agreed upon poem known to both the sender and receiver. The sender would pick words from the poem as the key and the words had letters that indicated that they are a keyword (the first word corresponds to A, the second is B and so on).
Example:
The poem is;
I compare thee to a summer’s day?
Thou art more lovely and more temperate
The keywords are:
I, to, day, art, temperate
The indicator group:
BEHJO
The keywords would be written out and numbered alphabetically to form a transposition key. The plaintext would then be written in the columns and the plaintext would be rewritten with the letters in each column in order with the indicator group written at the beginning.
Example continued:
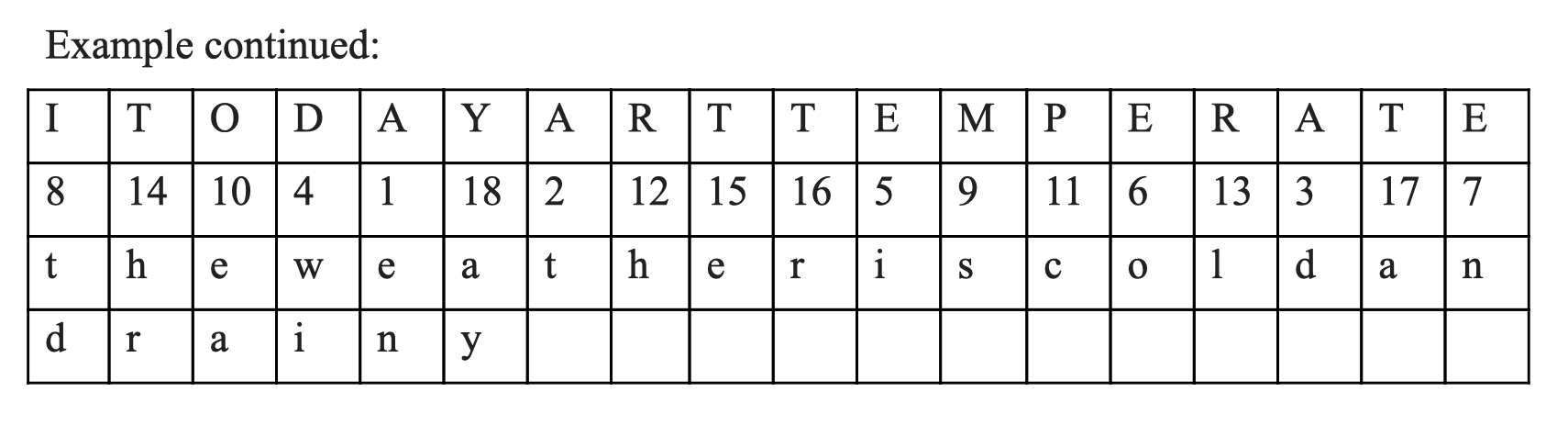 Ciphertext:
behjo entdw iiont dseac hlhre raay
This could be repeated multiple times to increase security and sometimes errors would be added to the poem so that, if the poem were revealed to the enemy, it would prevent the code from being broken. This method of encryption did not rely on a codebook unlike many other ciphers. The decryption was simply the reverse of the encryption process.
However, poem code did have its disadvantages. It was easily susceptible to human error and messages could not be shorter than 200 words, otherwise the encryption would not be secure enough. Poems were reused so, once a message was broken and the poem and intentional errors revealed, all messages past and present could be read, and this also led the code to be weak to cryptoanalysis. The use of famous poems also meant the code would be more likely to be broken.
United States of America
SIGABA
Ciphertext:
behjo entdw iiont dseac hlhre raay
This could be repeated multiple times to increase security and sometimes errors would be added to the poem so that, if the poem were revealed to the enemy, it would prevent the code from being broken. This method of encryption did not rely on a codebook unlike many other ciphers. The decryption was simply the reverse of the encryption process.
However, poem code did have its disadvantages. It was easily susceptible to human error and messages could not be shorter than 200 words, otherwise the encryption would not be secure enough. Poems were reused so, once a message was broken and the poem and intentional errors revealed, all messages past and present could be read, and this also led the code to be weak to cryptoanalysis. The use of famous poems also meant the code would be more likely to be broken.
United States of America
SIGABA SIGABA (also called ECM Mark II) was a cipher machine used by the United States from 1944 until the 1950s. It had an electromechanical system of rotors with significant improvements made on previous rotor machines such as Enigma. The SIGABA’s main difference from other rotor machines was that it had three banks of five rotors (fifteen in total) and the first two banks affected the stepping of the third. The stepping of the rotors being more complex meant that attacks which broke similar rotor machines with more simple stepping were not as effective.
One of the problems with SIGABA was that it was heavy, expensive and complex. As it was not easily transportable, it was commonly used in radio rooms of US Navy ships but could not be used in the field and was deemed excessive for tactical communications and so the M-209 was often used instead. However, evidence has emerged recently that the M-209 code was broken by the Germans in World War II whereas SIGABA has yet to be broken (at least publicly).
Code Talkers
Code talkers used languages that were used by an exceedingly small population of people as a way to communicate secretly. The United States service had roughly 500 Native American code talkers who used Native American languages to send secret communications during World War II. Code talkers used military telephone or radio communications nets with codes that were based on their native languages. As the encryption was based on a natural language, the secret communications were dealt with speeds that were significantly faster than when other methods of cryptography were used.
During World War II, there were two code types. Type one codes were developed from languages of the Hopi, Comanche, Navajo and Meskwaki peoples. It used a simple substitution cipher where each letter corresponded to a word from their languages. Type two code was a translation from English into the native language. Any words that would not translate directly would be described instead.
JAPAN
Type B Cipher Machine
SIGABA (also called ECM Mark II) was a cipher machine used by the United States from 1944 until the 1950s. It had an electromechanical system of rotors with significant improvements made on previous rotor machines such as Enigma. The SIGABA’s main difference from other rotor machines was that it had three banks of five rotors (fifteen in total) and the first two banks affected the stepping of the third. The stepping of the rotors being more complex meant that attacks which broke similar rotor machines with more simple stepping were not as effective.
One of the problems with SIGABA was that it was heavy, expensive and complex. As it was not easily transportable, it was commonly used in radio rooms of US Navy ships but could not be used in the field and was deemed excessive for tactical communications and so the M-209 was often used instead. However, evidence has emerged recently that the M-209 code was broken by the Germans in World War II whereas SIGABA has yet to be broken (at least publicly).
Code Talkers
Code talkers used languages that were used by an exceedingly small population of people as a way to communicate secretly. The United States service had roughly 500 Native American code talkers who used Native American languages to send secret communications during World War II. Code talkers used military telephone or radio communications nets with codes that were based on their native languages. As the encryption was based on a natural language, the secret communications were dealt with speeds that were significantly faster than when other methods of cryptography were used.
During World War II, there were two code types. Type one codes were developed from languages of the Hopi, Comanche, Navajo and Meskwaki peoples. It used a simple substitution cipher where each letter corresponded to a word from their languages. Type two code was a translation from English into the native language. Any words that would not translate directly would be described instead.
JAPAN
Type B Cipher Machine The Type B Cipher machine (named “Purple” by the United States) was an encryption machine, with three stages of stepping switches and a plugboard, that was used during World War II by the Japanese Foreign Office. It superseded the Type A Cipher machine “Red” and, due to their similarities and “Red” having been broken by the U.S. Army, there already was significant progress in breaking “Purple” by the start of the war. In September 1940, cryptographers were able to construct a machine that replicated the Japanese machines.
While the “Purple” machine was more secure than “Red”, the Japanese Navy rejected the idea that “Red” had been broken and so continued using “Red” alongside “Purple”. The “Purple” machine had the same flaw as the “Red” machine where six letters of the alphabet were encrypted separately to the rest but these letters were changed every nine days (Red’s six letters were fixed at 'a', 'e', 'i', 'o', 'u' and 'y'). It had two typewriters, one that was used for encryption and the other for decryption, as the ciphertext only had to go through the machine in reverse in order for it to be decrypted back into its plaintext.
Written by Kendal
The Type B Cipher machine (named “Purple” by the United States) was an encryption machine, with three stages of stepping switches and a plugboard, that was used during World War II by the Japanese Foreign Office. It superseded the Type A Cipher machine “Red” and, due to their similarities and “Red” having been broken by the U.S. Army, there already was significant progress in breaking “Purple” by the start of the war. In September 1940, cryptographers were able to construct a machine that replicated the Japanese machines.
While the “Purple” machine was more secure than “Red”, the Japanese Navy rejected the idea that “Red” had been broken and so continued using “Red” alongside “Purple”. The “Purple” machine had the same flaw as the “Red” machine where six letters of the alphabet were encrypted separately to the rest but these letters were changed every nine days (Red’s six letters were fixed at 'a', 'e', 'i', 'o', 'u' and 'y'). It had two typewriters, one that was used for encryption and the other for decryption, as the ciphertext only had to go through the machine in reverse in order for it to be decrypted back into its plaintext.
Written by Kendal