
The Diffie Hellman Key Exchange resolves the issue surrounding secure key transmission; using this method the key is never in the public domain. This method is used in conjunction with RSA and ECC, as well as other encryption methods.
Alice and Bob agree on a Generator G in the public domain. They can then separately choose their private keys, which are not shared at all. Their private keys and the generator can then be used to find their public keys, which can be shared publicly.
This concept is commonly explained using a colour metaphor, which we have used here to help visualise the operations performed to find the key.
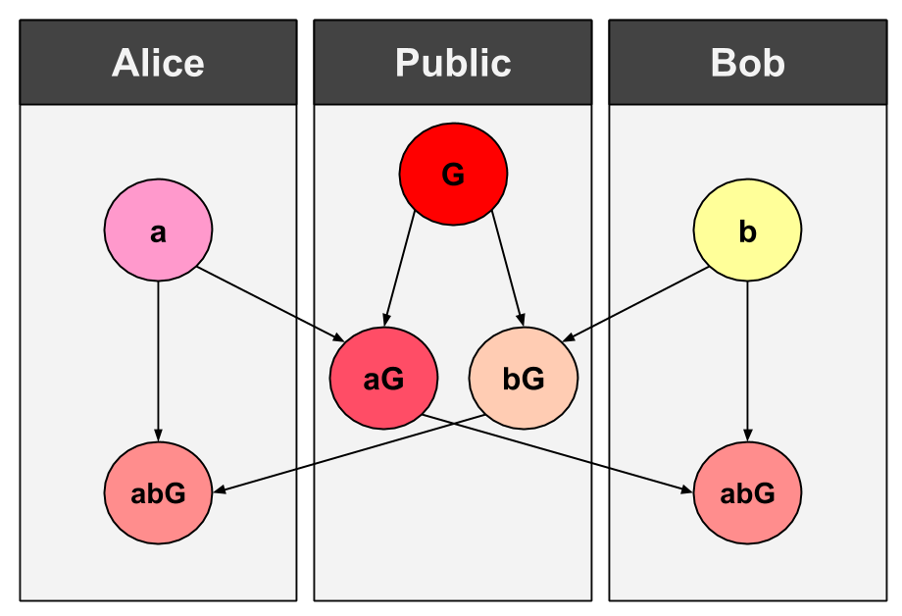 In the image above you can see that Alice and Bob have shared their public keys aG and bG respectively. An interceptor would not be able to work out their private keys from their public keys as the mathematics are easy one way but extremely difficult to reverse. The key abG is then found with a private key and the public key of the person you are communicating with. A private key is required to find the key so nobody in the public domain can find the key from any of the public parameters of the encryption.
Example:
In public Alice and Bob agree on a large prime p and a primitive root of p, g. In this example we will use p = 7 and g = 3.
Private keys are chosen such that a, b < p. In this example we will use, a = 2 and b = 4.
The following formula is used to calculate a public key where x is the private key:
In the image above you can see that Alice and Bob have shared their public keys aG and bG respectively. An interceptor would not be able to work out their private keys from their public keys as the mathematics are easy one way but extremely difficult to reverse. The key abG is then found with a private key and the public key of the person you are communicating with. A private key is required to find the key so nobody in the public domain can find the key from any of the public parameters of the encryption.
Example:
In public Alice and Bob agree on a large prime p and a primitive root of p, g. In this example we will use p = 7 and g = 3.
Private keys are chosen such that a, b < p. In this example we will use, a = 2 and b = 4.
The following formula is used to calculate a public key where x is the private key:
 Written by Chelsea
Written by Chelsea