
Asymmetric key encryption, also known as public-key encryption, is the process in which the different keys are used for encrypting and decrypting the information. The keys are mathematically related which allows the plaintext to be retrieved from decrypting the ciphertext without the need to pre-share the secret key.
 The algorithms are called ‘public-key’ because they are available to the public, but only the intended recipient with the corresponding decryption key can decrypt the message. In these systems, the encryption key is called the public key and the decryption key is called the private key. The public and private keys are related mathematically but it is computationally impossible to find one from the other, hence why asymmetric encryption is much stronger.
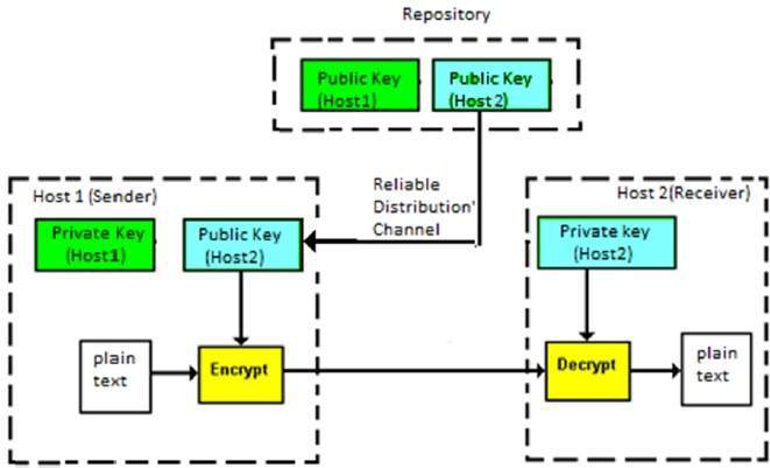
Following the image, when Host1 sends a message to Host2, the public key of Host2 is obtained from the public repository, the data is encrypted and transmitted. Host2 uses their private key to extract the plaintext once the ciphertext is received. This communication requires trust between the parties that the public key used is that of the intended recipient. Malicious attackers can spoof public keys to obtain messages and creates a problem for asymmetric cryptosystems.
To ensure trust, a Public Key Infrastructure (PKI) is used by third parties to attain the authenticity of public keys. When the third party is requested to provide a public key for external communication, they are trusted to provide the correct public key. The third party can satisfy the user identity of the other person through methods of attestation, notarisation or any process that identifies that the person is globally unique. A common method for making verified public keys is to embed them into a digital website signature.
Due to the advantages and disadvantages of both key systems, both symmetric and public-key cryptosystems are often used together in information security infrastructures.
Written by JaneW
The algorithms are called ‘public-key’ because they are available to the public, but only the intended recipient with the corresponding decryption key can decrypt the message. In these systems, the encryption key is called the public key and the decryption key is called the private key. The public and private keys are related mathematically but it is computationally impossible to find one from the other, hence why asymmetric encryption is much stronger.
Following the image, when Host1 sends a message to Host2, the public key of Host2 is obtained from the public repository, the data is encrypted and transmitted. Host2 uses their private key to extract the plaintext once the ciphertext is received. This communication requires trust between the parties that the public key used is that of the intended recipient. Malicious attackers can spoof public keys to obtain messages and creates a problem for asymmetric cryptosystems.
To ensure trust, a Public Key Infrastructure (PKI) is used by third parties to attain the authenticity of public keys. When the third party is requested to provide a public key for external communication, they are trusted to provide the correct public key. The third party can satisfy the user identity of the other person through methods of attestation, notarisation or any process that identifies that the person is globally unique. A common method for making verified public keys is to embed them into a digital website signature.
Due to the advantages and disadvantages of both key systems, both symmetric and public-key cryptosystems are often used together in information security infrastructures.
Written by JaneW