
The history of cryptology is thought to date back to Egyptian times, almost 4000 years ago, when human beings discovered the art of writing. Originating from the Greek words kryptós (meaning ‘hidden’), and lógos (meaning ‘word’), cryptology is the science that studies secure and secret data communication and storage in the form of a cryptosystem.
Hidden or secret messaging evolved with civilisations as they formed tribes, groups and kingdoms which required power, politics and battles to be upheld. This resulted in secrecy when passing communications between people and the development of cryptography, particularly from the Romans and Egyptians as the hieroglyph is thought to be the first evidence of cryptography. The intent of the hieroglyphs was not to conceal messages but since it took hundreds of years to solve the meaning of the characters, it can be considered as one of the earliest forms of cryptography.
 Moving to Roman times, around 100 BC, Julius Caesar developed his own method of encryption so he could communicate with the generals of his armies on the war front, without enemies knowing. This form of encryption became known as the Caesar Cipher and relied on letter shifting, by an agreed number (3 being a common choice), and substitution so the letters became jumbled up. For example, character was shifted by 3 places, so the character 'A' was replaced by 'D', 'B' was replaced by 'E', and so on. The characters would wrap around at the end, so 'X' would be replaced by 'A'.
Moving to Roman times, around 100 BC, Julius Caesar developed his own method of encryption so he could communicate with the generals of his armies on the war front, without enemies knowing. This form of encryption became known as the Caesar Cipher and relied on letter shifting, by an agreed number (3 being a common choice), and substitution so the letters became jumbled up. For example, character was shifted by 3 places, so the character 'A' was replaced by 'D', 'B' was replaced by 'E', and so on. The characters would wrap around at the end, so 'X' would be replaced by 'A'.
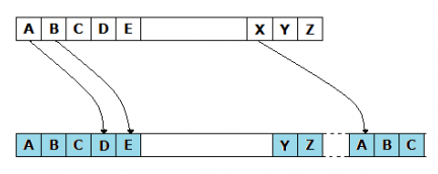 However, this cipher became quite easy to crack. Once the shared number was known, the recipient or interceptor could decode the message.
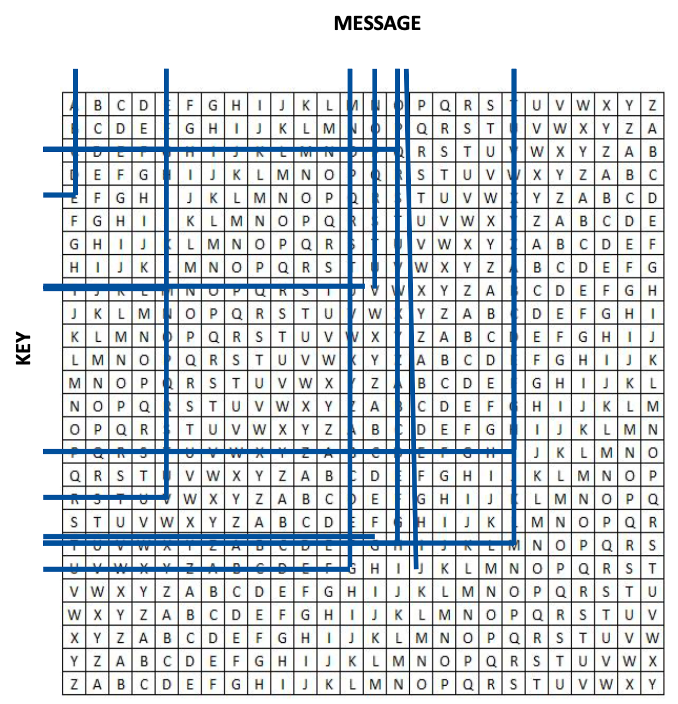
The 16th century brought a new cipher, known as Vigenère’s cipher, which is thought to be the first cipher that required a key to encrypt and decrypt the message. It used polyalphabetic substitution meaning several alphabets were required to substitute letters, usually in the form of a Vigenère square. The square consists of the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar Ciphers.
However, this cipher became quite easy to crack. Once the shared number was known, the recipient or interceptor could decode the message.
The 16th century brought a new cipher, known as Vigenère’s cipher, which is thought to be the first cipher that required a key to encrypt and decrypt the message. It used polyalphabetic substitution meaning several alphabets were required to substitute letters, usually in the form of a Vigenère square. The square consists of the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar Ciphers.
 The square is useless unless you are aware of the key which helps you to cross-reference letters and then decrypt the encrypted message. For example, if we want to encrypt the message “Meet me at noon” using the key “picture”, using the square we get the cipher text “BMGM GV EI VQHH”.
The square is useless unless you are aware of the key which helps you to cross-reference letters and then decrypt the encrypted message. For example, if we want to encrypt the message “Meet me at noon” using the key “picture”, using the square we get the cipher text “BMGM GV EI VQHH”.
 M E E T M E A T N O O N
P I C T U R E P I C T U
B M G M G V E I V Q H H
Vigenère ciphers were also easy to crack but the use of a keyword to encrypt the data made it much more secure than the Caesar cipher.
Encryption became much more sophisticated after the 19th century as more machines became electric. Cryptography changed from being ‘makeshift’ ideas to the more scientific process we know and use today. The early 20th century brought along the Enigma rotor machine with World War I and it became heavily used in German communications in World War II. The rotors within the machine provided more advanced and efficient means of coding the information.
During the period of World War II, both cryptography and cryptanalysis became excessively mathematical and advances in the field led to cryptographic implementation within government organisations, military units, and some large corporate businesses. Now, the arrival of computers and the Internet has brought effective cryptography within the reach of common people and takes us onto the crypto wars.
Written by JaneW
M E E T M E A T N O O N
P I C T U R E P I C T U
B M G M G V E I V Q H H
Vigenère ciphers were also easy to crack but the use of a keyword to encrypt the data made it much more secure than the Caesar cipher.
Encryption became much more sophisticated after the 19th century as more machines became electric. Cryptography changed from being ‘makeshift’ ideas to the more scientific process we know and use today. The early 20th century brought along the Enigma rotor machine with World War I and it became heavily used in German communications in World War II. The rotors within the machine provided more advanced and efficient means of coding the information.
During the period of World War II, both cryptography and cryptanalysis became excessively mathematical and advances in the field led to cryptographic implementation within government organisations, military units, and some large corporate businesses. Now, the arrival of computers and the Internet has brought effective cryptography within the reach of common people and takes us onto the crypto wars.
Written by JaneW