The Advanced Encryption Standard (AES) is a symmetric block cipher which is used by the U.S. government to protect classified information. The National Institute of Standards and Technology (NIST) started development of AES in 1997 when it announced the need for an alternative to the Data Encryption Standard (DES), which was starting to become vulnerable to brute-force attacks. It is also at least six time faster than triple DES.
AES is based on a substitution–permutation network. It is comprised of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations). AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. These 16 bytes are arranged in four columns and four rows.
How does AES work?
An important aspect of AES is the substitutions that are made, knows as an S-box. This substitution process derives from the Rijndael cipher, on which the AES cryptographic algorithm is based. Rijndael was created by the Belgian cryptologists, Vincent Rijmen and Joan Daemen, and was achieved through a series of martix transformations.
 The permutation aspect of the cipher uses a P-box. P-boxes are a method of bit-shuffling used to permute or transpose bits across S-boxes inputs, retaining diffusion while transposing.
The permutation aspect of the cipher uses a P-box. P-boxes are a method of bit-shuffling used to permute or transpose bits across S-boxes inputs, retaining diffusion while transposing.
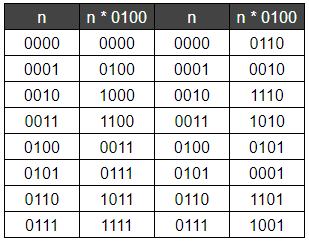 If the P-Box input is n1 and n2, the first nibble out m1 = n1 XOR n2 * 0100, the second m2 = n1 * 0100 XOR n2
Let's have a look at an example of the AES cipher.
Key Generation
Please note, this is an example of Simplified-AES or S-AES and the operations performed do not vary from those performed with a larger key length.
We begin with an initial key K0, of length 16 bits which split in half are referred to as W0 and W1. We take W1 and swap the order of the nibbles (a nibble is 4 bits).
If the P-Box input is n1 and n2, the first nibble out m1 = n1 XOR n2 * 0100, the second m2 = n1 * 0100 XOR n2
Let's have a look at an example of the AES cipher.
Key Generation
Please note, this is an example of Simplified-AES or S-AES and the operations performed do not vary from those performed with a larger key length.
We begin with an initial key K0, of length 16 bits which split in half are referred to as W0 and W1. We take W1 and swap the order of the nibbles (a nibble is 4 bits).
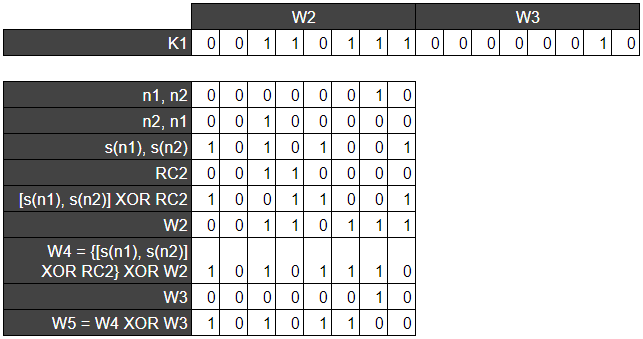
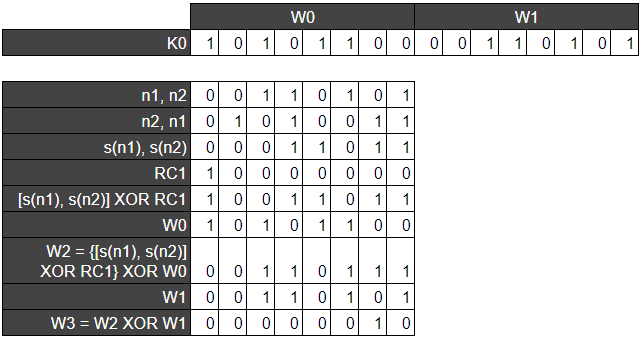 The nibbles are then substituted using the S-Boxes and XOR’d with the round constant. The result of this operation is then XOR’d with W0 to find W2 (the first half of the next key). W3 is found by XORing W2 and W1. This process is repeated until enough keys have been generated for the encryption.
The nibbles are then substituted using the S-Boxes and XOR’d with the round constant. The result of this operation is then XOR’d with W0 to find W2 (the first half of the next key). W3 is found by XORing W2 and W1. This process is repeated until enough keys have been generated for the encryption.
 Encryption
In a round of AES encryption there are four steps, which you need to repeat for every round:
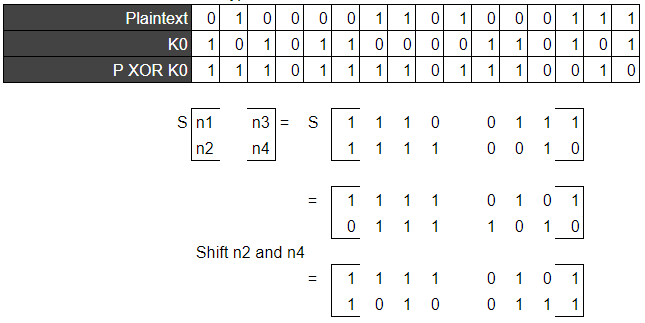
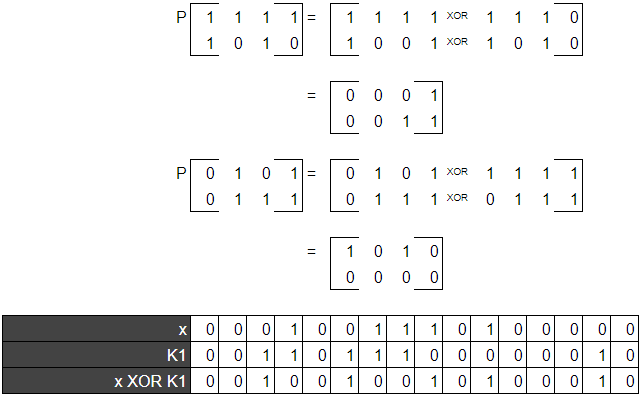
Step 1: XOR your plaintext (or the result of the last round) with the round key.
Step 2: Put each of the four nibbles in a 2x2 matrix and input each into a S-Box.
Step 3: Shift the nibbles (swap n2 and n4).
Step 4: Input the nibbles into a P-Box (NOTE: Omit step 4 in the last round).
Encryption
In a round of AES encryption there are four steps, which you need to repeat for every round:
Step 1: XOR your plaintext (or the result of the last round) with the round key.
Step 2: Put each of the four nibbles in a 2x2 matrix and input each into a S-Box.
Step 3: Shift the nibbles (swap n2 and n4).
Step 4: Input the nibbles into a P-Box (NOTE: Omit step 4 in the last round).
 If you visit our programming tab, you can learn how to implement AES in Python.
Written by Chelsea and JaneW
If you visit our programming tab, you can learn how to implement AES in Python.
Written by Chelsea and JaneW







