
This follows on after the WWII cryptography history lessons in chronological order. Unless you specifically want information on the crypto wars, please read our WWII section. Crypto Wars is a 5 part section spread over multiple webpages.
This section serves to focus on providing knowledge of the crypto wars, as well as other events occurring around the time to allow you to understand the context and draw your conclusions from this topic. Many other online sources of the Crypto Wars will not break down current events and would require additional research - we’ve taken care of that for you. Everything you need on the ongoing Crypto Wars will be right here.
The Beginning
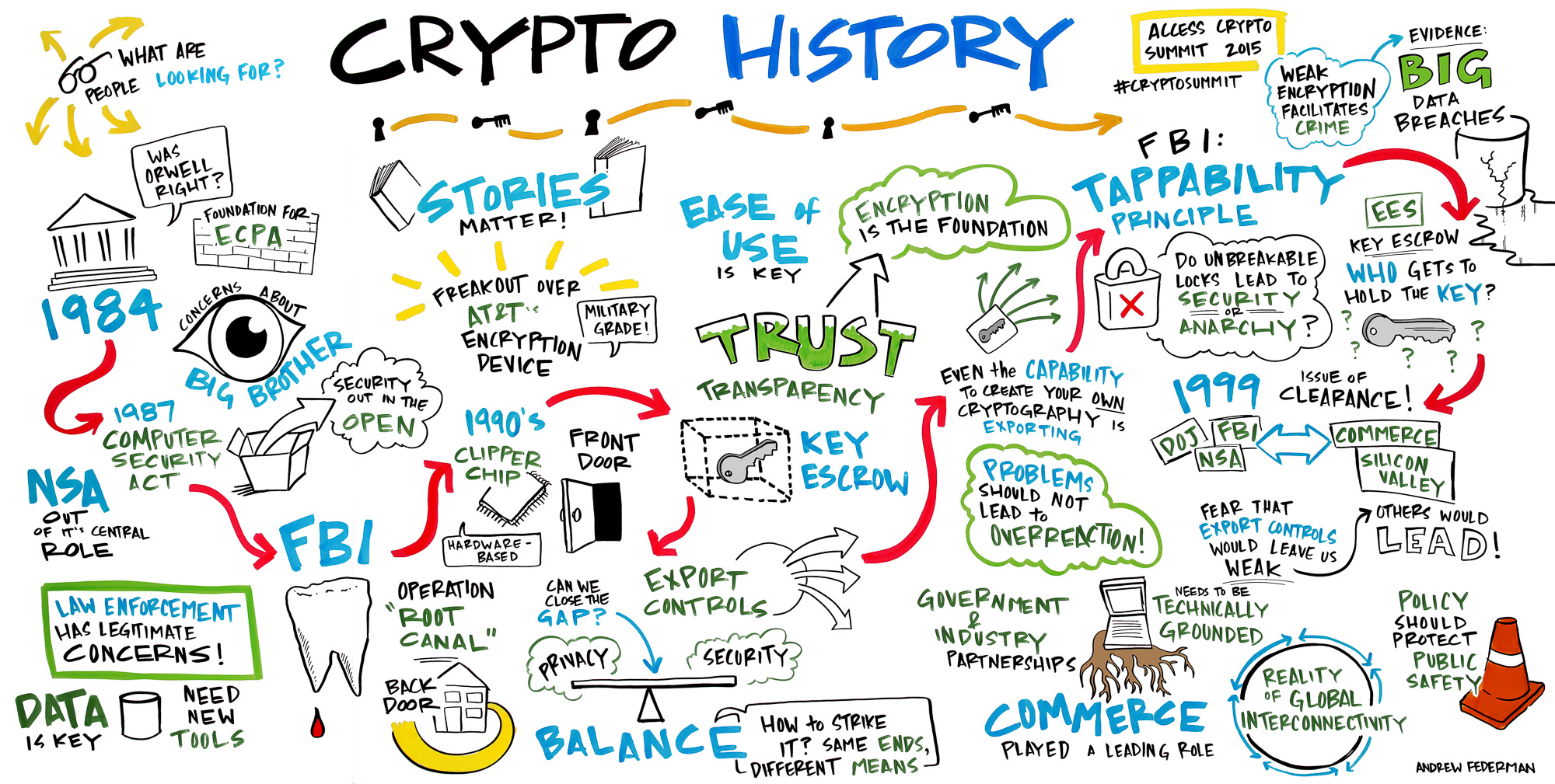 The crypto wars is an ongoing series of “wars” where the commercial sector and general public disagree with their government, and engage in diplomacy or activism against them; dating back as early as 1954.
Let’s cast our minds back as we set the scene. It’s November 1954, the United States of America is under pressure to limit exports of military goods to other countries following the Truman Doctrine in 1947. After battling in two world wars, and still facing extreme pressure by the Soviet Union, the U.S. placed cryptography on the U.S. Munitions List under ‘Auxiliary Military Equipment’. Following Britain’s success in breaking the Enigma cypher in WWII, which significantly counted towards the Allies success. The U.S. and U.K. wanted to protect their advancements in cryptography by blocking other countries from accessing their secrets. This did lead to many issues, but we’ll get to that later.
So, it’s 1954, for reference the Cuban missile crisis occurred in 1962. Hence, the Cold War between U.S. and Russia was well underway. They were developing new technologies to scare each other with Mutually Assured Destruction (MAD) and trying to grasp as much power as possible. This wasn’t seen as much of a significant issue by any party as encryption research had primarily been in the hands of the military and government only. Many cryptographic protocol types such as RSA, ECC, and PGP didn’t exist at this time, simply because many people didn’t yet have a necessity to encrypt their data.
The crypto wars is an ongoing series of “wars” where the commercial sector and general public disagree with their government, and engage in diplomacy or activism against them; dating back as early as 1954.
Let’s cast our minds back as we set the scene. It’s November 1954, the United States of America is under pressure to limit exports of military goods to other countries following the Truman Doctrine in 1947. After battling in two world wars, and still facing extreme pressure by the Soviet Union, the U.S. placed cryptography on the U.S. Munitions List under ‘Auxiliary Military Equipment’. Following Britain’s success in breaking the Enigma cypher in WWII, which significantly counted towards the Allies success. The U.S. and U.K. wanted to protect their advancements in cryptography by blocking other countries from accessing their secrets. This did lead to many issues, but we’ll get to that later.
So, it’s 1954, for reference the Cuban missile crisis occurred in 1962. Hence, the Cold War between U.S. and Russia was well underway. They were developing new technologies to scare each other with Mutually Assured Destruction (MAD) and trying to grasp as much power as possible. This wasn’t seen as much of a significant issue by any party as encryption research had primarily been in the hands of the military and government only. Many cryptographic protocol types such as RSA, ECC, and PGP didn’t exist at this time, simply because many people didn’t yet have a necessity to encrypt their data.
 However, this did change. Let’s take you forwards 21 years to 1977 to present Data Encryption Standard (DES). DES is the U.S. Government’s first publicly accessible encryption algorithm standard created and published by IBM.
DES or Data Encryption Standard (we cover DES on another page, make sure to check that out!) was released to the United States’ population for use as a government-sponsored encryption technique. Introduced as a 40/56 bit key (with an 8-bit checksum resulting in 48/64 bit keys) it was accepted by the American public for regular use. It quickly spread internationally for the citizens and governments of other countries to use unofficially. Lucifer’s key, which was the block cypher (symmetric encryption algorithm) created by Horst Feistel and IBM, was placed at a block size of 128. This key was used to develop DES; however, the NSA reduced the block size to either 48/64 (with a cypher size of 40/56) before DES was designed around this new Feistel-network version of Lucifer key. The NSA did attempt to make a block size of 48 the norm, but IBM compromised on 56 as their standard. The NSA still pushed for the American standard to be a block size of 48 bits.
However, this did change. Let’s take you forwards 21 years to 1977 to present Data Encryption Standard (DES). DES is the U.S. Government’s first publicly accessible encryption algorithm standard created and published by IBM.
DES or Data Encryption Standard (we cover DES on another page, make sure to check that out!) was released to the United States’ population for use as a government-sponsored encryption technique. Introduced as a 40/56 bit key (with an 8-bit checksum resulting in 48/64 bit keys) it was accepted by the American public for regular use. It quickly spread internationally for the citizens and governments of other countries to use unofficially. Lucifer’s key, which was the block cypher (symmetric encryption algorithm) created by Horst Feistel and IBM, was placed at a block size of 128. This key was used to develop DES; however, the NSA reduced the block size to either 48/64 (with a cypher size of 40/56) before DES was designed around this new Feistel-network version of Lucifer key. The NSA did attempt to make a block size of 48 the norm, but IBM compromised on 56 as their standard. The NSA still pushed for the American standard to be a block size of 48 bits.
