
Symmetric key encryption, also known as secret key encryption, is the process in which the same keys are used for encrypting and decrypting the information. It requires the sender and receiver to agree on a key before they can communicate securely. Prior to the 1970s, symmetric key encryption was implemented in all cryptosystems and is still widely used today. An example of symmetric key encryption includes Digital Encryption Standard (DES) and follows a simple model.
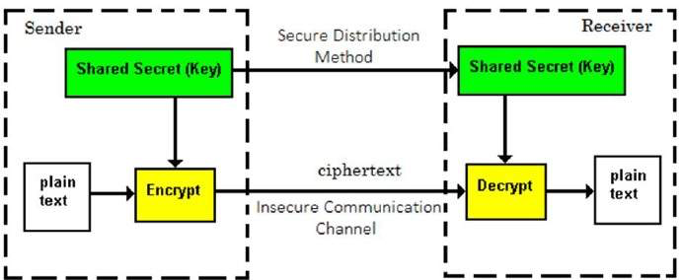 There are several advantages to using a symmetric cryptosystem with some of the main features including;
• Users share a common key to exchange information. It is recommended that keys are changed regularly to prevent attack on a system however, this can become expensive as the mechanism required to exchange the key will also need to be changed.
• In a group of n users, to enable communication between any two users, the number of keys required for the group is (n(n-1))/2.
• The length of the key (number of bits) depends on the type of symmetric algorithm. Generally symmetric keys can be split into two categories, stream ciphers and block ciphers. Stream ciphers operate in single bits whereas block ciphers operate in groups of bits, which in a modern computer is typically 64 bits. Symmetric algorithms are also smaller than asymmetric algorithms so run faster and therefore require less processing power of the computer system.
Despite these advantages, there are two challenges with symmetric algorithms that are highly restrictive in modern day communication – key establishment and trust issues.
Before any communication can take place between parties, both the sender and receiver must agree on a secret key which requires a secure key establishment mechanism. Without this key, the message either will remain decrypted or remain encrypted as related keys have not been used. Additionally, there must be a degree of ‘trust’ within the relationship between the sender and receiver as the same key is to be used. This poses a problem as modern day communication requires information to be exchanged between non-familiar and non-trusted parties. Such limitations gave rise to asymmetric key encryption systems.
Written by JaneW
There are several advantages to using a symmetric cryptosystem with some of the main features including;
• Users share a common key to exchange information. It is recommended that keys are changed regularly to prevent attack on a system however, this can become expensive as the mechanism required to exchange the key will also need to be changed.
• In a group of n users, to enable communication between any two users, the number of keys required for the group is (n(n-1))/2.
• The length of the key (number of bits) depends on the type of symmetric algorithm. Generally symmetric keys can be split into two categories, stream ciphers and block ciphers. Stream ciphers operate in single bits whereas block ciphers operate in groups of bits, which in a modern computer is typically 64 bits. Symmetric algorithms are also smaller than asymmetric algorithms so run faster and therefore require less processing power of the computer system.
Despite these advantages, there are two challenges with symmetric algorithms that are highly restrictive in modern day communication – key establishment and trust issues.
Before any communication can take place between parties, both the sender and receiver must agree on a secret key which requires a secure key establishment mechanism. Without this key, the message either will remain decrypted or remain encrypted as related keys have not been used. Additionally, there must be a degree of ‘trust’ within the relationship between the sender and receiver as the same key is to be used. This poses a problem as modern day communication requires information to be exchanged between non-familiar and non-trusted parties. Such limitations gave rise to asymmetric key encryption systems.
Written by JaneW