
Cracking DES
*Sigh* no, no it wasn’t... the story rages on. See, encryption was now not on the munitions list. However, the government still required that a licence had to be issued before the export of encryption was legal. Their view at the time was that encryption could be as secure as you wanted, but it has to be 40-bit. If you remember earlier, we mentioned that “useful encryption algorithms have both of the following, strong mathematics, and large key sizes”. This meant that other standards might be more reliable than DES; they wouldn’t be working to their full potential. As the government pushed for the idea that 40-bit encryption was more than adequate; In truth, many, many more bits were required to protect encryption algorithms. So, here came the time to prove them wrong.
 I’m going to quickly switch back to the U.K.’s perspective, as, until 1996, the export of cryptography was banned until a debate around the use of cryptography in the NHS brought it to light. The U.K.’s Government lost it’s a stronghold on cryptography while the country grew its encryption power.
I’m going to quickly switch back to the U.K.’s perspective, as, until 1996, the export of cryptography was banned until a debate around the use of cryptography in the NHS brought it to light. The U.K.’s Government lost it’s a stronghold on cryptography while the country grew its encryption power.
 Many challenges were set to try to crack DES; the first major one was established by RSA (ring a bell?) Security who offered a reward if someone came forwards with a way to defeat 40-bit DES. A group managed to break DES within 39 days in 1997, with others. So, DES cracked! This was taken to NIST who replied with that 39 days was too long to crack a DES key for it to be considered a plausible threat. So more challenges were issued to find a way to break DES quicker so that the U.S. Government Security Agencies would finally listen. The EFF even created a tool called the DES cracker which is still partially around to this day (DES is used to a small extent over the internet, but with larger key sizes. Deep Crack (the name of DES cracker) was able to go through 90 billion keys per second by utilising the power of 29 circuit boards with 64 hips each! EFF submitted the cracker to one of these competitions ran by RSA Security, and they won a prize of $10,000. Quite insignificant considering that the project costs around $250,000 to make each machine, but it was the price to pay for stronger encryption. So, with this processing power, it should go through all DES keys of this length within 9 days, but using balance of probability, it would average at 4.5 days for each key.
Many challenges were set to try to crack DES; the first major one was established by RSA (ring a bell?) Security who offered a reward if someone came forwards with a way to defeat 40-bit DES. A group managed to break DES within 39 days in 1997, with others. So, DES cracked! This was taken to NIST who replied with that 39 days was too long to crack a DES key for it to be considered a plausible threat. So more challenges were issued to find a way to break DES quicker so that the U.S. Government Security Agencies would finally listen. The EFF even created a tool called the DES cracker which is still partially around to this day (DES is used to a small extent over the internet, but with larger key sizes. Deep Crack (the name of DES cracker) was able to go through 90 billion keys per second by utilising the power of 29 circuit boards with 64 hips each! EFF submitted the cracker to one of these competitions ran by RSA Security, and they won a prize of $10,000. Quite insignificant considering that the project costs around $250,000 to make each machine, but it was the price to pay for stronger encryption. So, with this processing power, it should go through all DES keys of this length within 9 days, but using balance of probability, it would average at 4.5 days for each key.
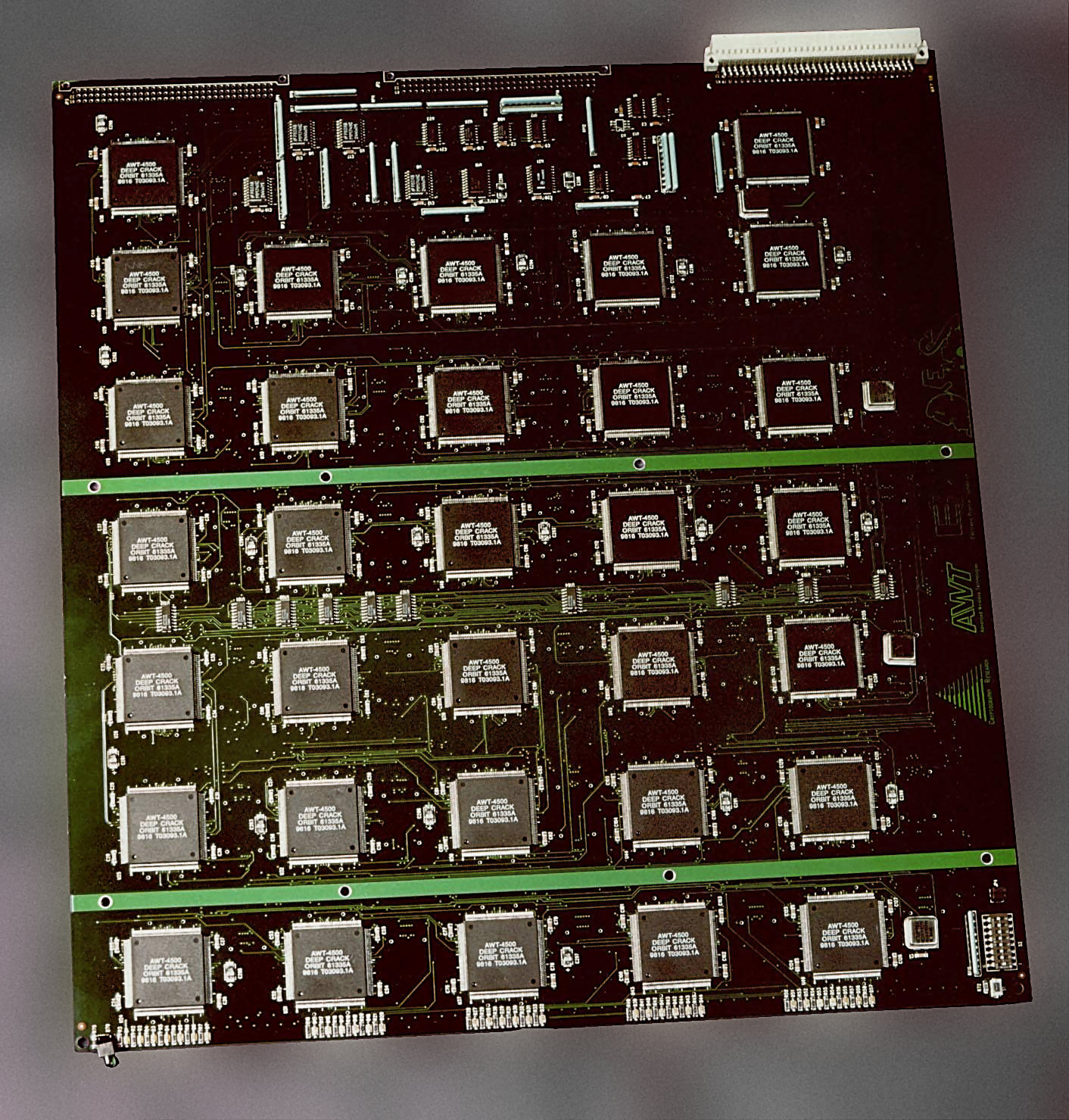 Just for your amusement, during the whole DES ordeal, the NSA thought that it would cost 20 million USD to create a bypass for DES, which, by the way, is pocket money for a foreign state. In 1998 when Deep Crack was designed, it cost horrendously less. It truly showed a lack of foresight by these governmental agencies. This device really put people and companies on edge; if a group could create a government standard cracking device in their eyes, they had total power. The real kicker is that the EFF built this to show what criminal masterminds could do; nothing was stopping them. This was still not enough for the U.S. Government to rescind it as their standard and claimed that it had to take less than 24 hours to crack for them to make a move. Deep crack had managed to crack a DES encryption in just 56 hours; so the first team that won and EFF joined together to destroy the U.S’ stance on 40-bit DES.
This is the final battle of the 20th century during the crypto wars. The team managed it; breaking the cypher in just under 22 hours, which cascaded through the government agencies rapidly. It led to new legislation around cryptography as well as the introduction of AES, the Advanced Encryption Standard. AES used a 120-bit cypher which was inherently stronger than DES. Triple DES was also allowed to be used, it used a 120-bit encryption key, but it still wasn’t as robust as the AES standard. In 1999 all ongoing court cases were dropped by the U.S. Government, and in 2000, as a finale, licensing was no longer required, and there wasn’t a restriction on key-lengths.
Just for your amusement, during the whole DES ordeal, the NSA thought that it would cost 20 million USD to create a bypass for DES, which, by the way, is pocket money for a foreign state. In 1998 when Deep Crack was designed, it cost horrendously less. It truly showed a lack of foresight by these governmental agencies. This device really put people and companies on edge; if a group could create a government standard cracking device in their eyes, they had total power. The real kicker is that the EFF built this to show what criminal masterminds could do; nothing was stopping them. This was still not enough for the U.S. Government to rescind it as their standard and claimed that it had to take less than 24 hours to crack for them to make a move. Deep crack had managed to crack a DES encryption in just 56 hours; so the first team that won and EFF joined together to destroy the U.S’ stance on 40-bit DES.
This is the final battle of the 20th century during the crypto wars. The team managed it; breaking the cypher in just under 22 hours, which cascaded through the government agencies rapidly. It led to new legislation around cryptography as well as the introduction of AES, the Advanced Encryption Standard. AES used a 120-bit cypher which was inherently stronger than DES. Triple DES was also allowed to be used, it used a 120-bit encryption key, but it still wasn’t as robust as the AES standard. In 1999 all ongoing court cases were dropped by the U.S. Government, and in 2000, as a finale, licensing was no longer required, and there wasn’t a restriction on key-lengths.
 The cypherpunks won the 20th-century crypto wars. Peter Junger could accept international students into his class, Zimmermann was able to publish his PGP code without government interference. The most significant achievement by far was that both the public and organisations were finally able to encrypt their data with a standard strong enough for them. Honestly, we have the EFF and cypherpunks to thank for the advancement of modern-day cryptography.
This concludes the 20th-century crypto wars, but, the title says ongoing, what’s up with that? Well, the government has been trying in many public and secret ways to attack cryptography, we will just highlight a few of these stories now, as they aren’t as prolific as the start of the crypto wars.
Written by HarryIsSecured
The cypherpunks won the 20th-century crypto wars. Peter Junger could accept international students into his class, Zimmermann was able to publish his PGP code without government interference. The most significant achievement by far was that both the public and organisations were finally able to encrypt their data with a standard strong enough for them. Honestly, we have the EFF and cypherpunks to thank for the advancement of modern-day cryptography.
This concludes the 20th-century crypto wars, but, the title says ongoing, what’s up with that? Well, the government has been trying in many public and secret ways to attack cryptography, we will just highlight a few of these stories now, as they aren’t as prolific as the start of the crypto wars.
Written by HarryIsSecured